
Top Cybersecurity Services in Detroit, MI
Cybersecurity services in Detroit by Bizionic Technologies include security solution implementations alongside comprehensively managed security services to safeguard businesses against risks posed by misconfigurations and inadequate change controls, a lack of cloud security architecture and strategy, insufficient identity and access management controls, account hijacking, insecure interfaces and APIs, malicious use of cloud services, and insider threats.
Bizionic Security Solutions
Bizionic Cloud Security Services Maximize The Use of The Cloud
Bizionic Technologies offers security solution implementations and dedicated managed security services to safeguard against risks posed by misconfigurations and inadequate change controls, a lack of cloud security architecture and strategy, insufficient identity and access management controls, account hijacking, insecure interfaces and APIs, malicious use of cloud services, and insider threats.
Comprehensive Digital Security Solutions
Cyber Security
Securing corporate networks and IT assets is vital in the ever-changing cybersecurity landscape. Regular security assessments can be a crucial frontline defense against ransomware

Cloud Security
To integrate cloud computing into your enterprise security program, evaluate resources and business needs to develop a fresh approach to your cloud security strategy.

Database Security
Ensuring your database s security is crucial to keeping your data safe. We boost your database security by using encryption, setting up access controls, doing regular security check-ups, and keeping your software up-to-date.

Application Security
To protect sensitive data and prevent unwanted access, application security must be ensured. We use some strong authentication methods to make your application more secure.

Compliance as a Service
Get comprehensive risk compliance and governance services. Maintain seamless compliance with changing security and regulatory requirements to safeguard your IT assets.

SeCops Solutions and Services
Adopt security with intention. Organize operations and development processes for on-premises and different cloud environments by integrating security and operations teams.
We Work Closely With Your Environment
Bizionic security detection is pluggable into your existing environment.
We use third-party technology, bizionic technologies,and any combination of the two.
OCI Services:
(Oracle Cloud Infrastructure (OCI) Services from Bizionic Technologies)
Transform your ITOps model to achieve increased scalability, agility, and compliance on OCI through OpEx.
Bizionic offers the following security solutions for OCI.
Create and construct a secure foundation for the network, storage, and processing that are essential to OCI. Evaluate, reinforce, and put into practice secure solutions the security posture. To prevent manual mistakes, automate the provision of certificates to linked services. Use threat intelligence information to implement threat protection. Oversee compliance and security standards for Oracle databases. Recognize, assess, and address security occurrences and events.

Maximize AWS Security with Bizionic Solutions:
Bizionic Technologies uses these technologies to assist your network and application security teams in meeting specific protection and compliance requirements within the AWS cloud. We offer comprehensive security solutions on the host, network, and application levels.
Bizionic Technologies: Your Gateway to Powerful AWS Security Services.
Bizionic Technologies enables you to fully utilize the capabilities of AWS Security Hub, a centralized platform within the AWS environment. Security Hub not only collects, organizes, and prioritizes security alerts and results from a wide range of AWS security services, but it also interfaces with third-party partner products to provide a extensive view of your cloud security posture. This powerful tool gives you control over your cloud security, allowing you to make educated decisions.

Enhance your Azure identity with Bizionic Solutions:
Bizionic Technologies can set up Azure Active Directory (Azure AD) to centrally manage user identities and access rights. This ensures that only authorized users have access to your systems, data, and applications. They can also enable multi-factor authentication (MFA) as an additional layer of protection during sign- in.
Maintain Secure Communication and Data Encryption.
Bizionic Technologies will ensure that all communication between user devices and Microsoft data centers, as well as within the data centers, is secured using industry-standard protocols. They may also assist you select the best data encryption solution (up to AES-256) for your data at rest, providing you complete control over your security posture.
Protect your networks. Bizionic Technologies can use Azure's secure network infrastructure to connect your virtual machines (VMs) and on-premises data centers effortlessly. Azure actively prevents illegal traffic with powerful technologies, whereas Azure Virtual Network connects your on-premises network to the cloud via a secure site-to-site VPN connection

Protect your Salesforce using Bizionic Technologies' expertise:
Many firms underestimate the security dangers connected with Salesforce, exposing critical data. Bizionic Technologies will assist you in implementing strong Salesforce application security measures to secure your data from external attackers.
Understanding Salesforce's Security Needs
Salesforce provides access to a variety of people, including customers, partners, and suppliers. This interconnection exposes potential security vulnerabilities. Bizionic Technologies will assist you in identifying these vulnerabilities and implementing best-practice mitigation strategies.

Ransomware Surge
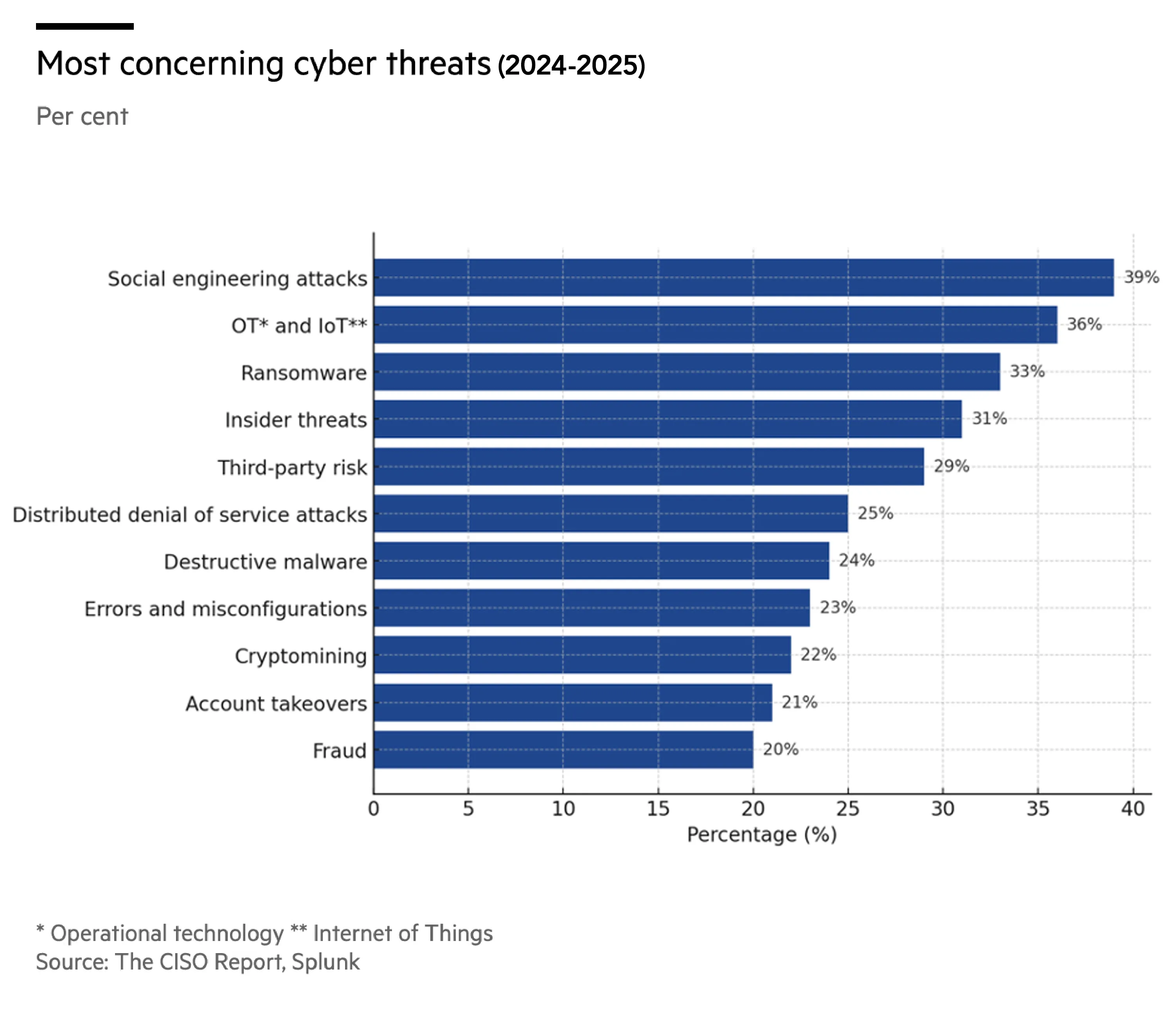
Most Concerning Cyber Threats
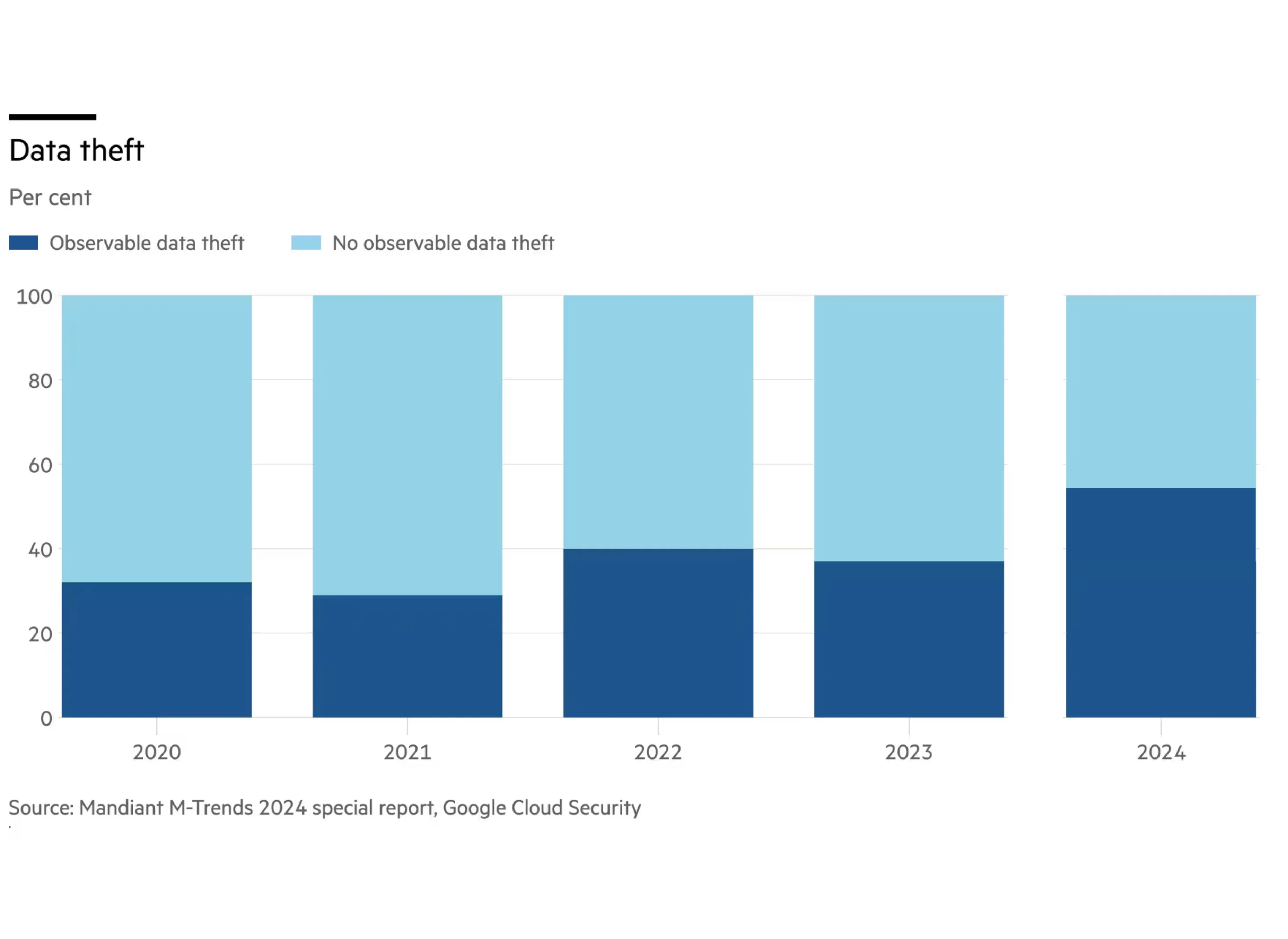
Data Thefts
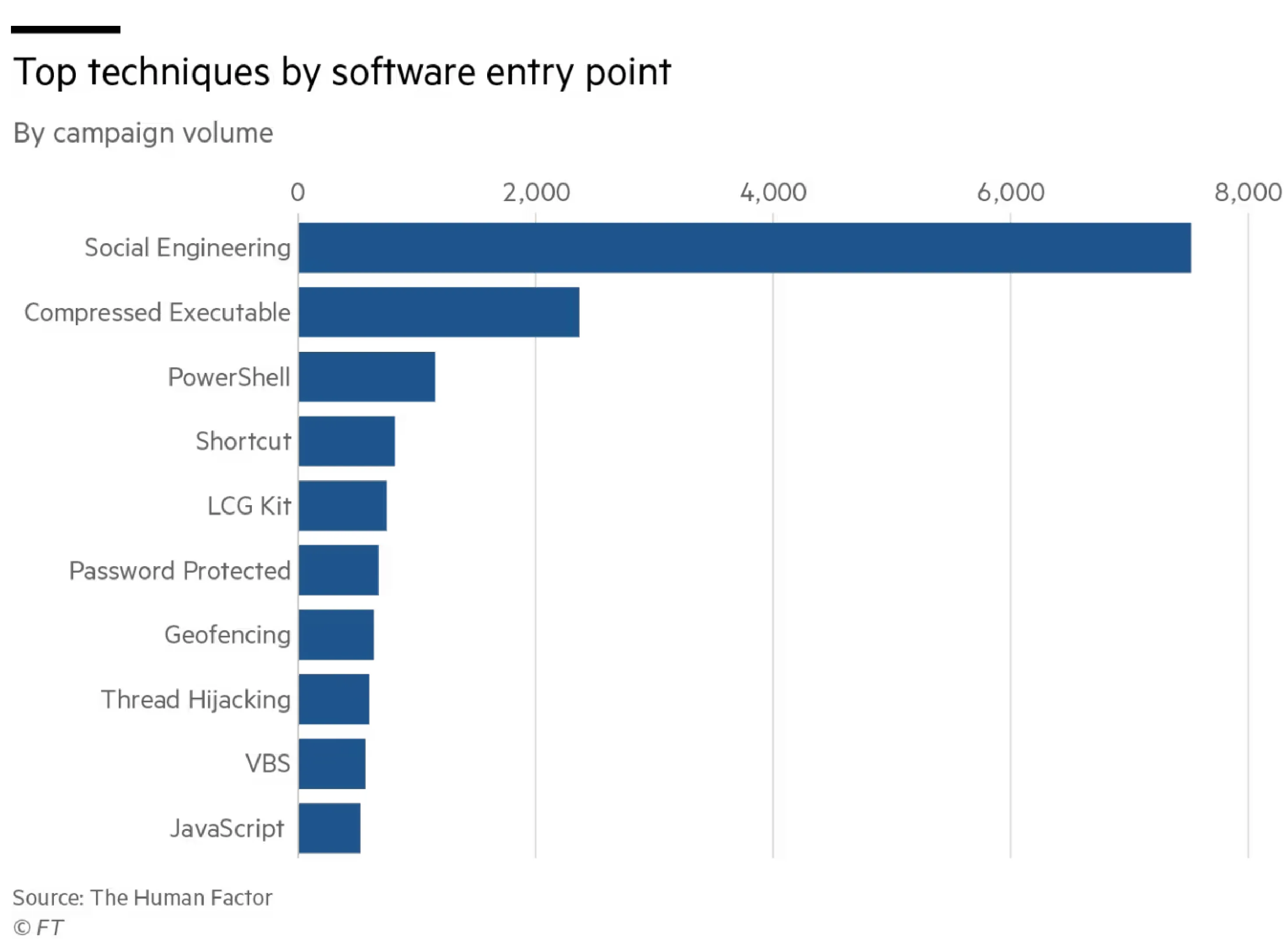
Techniques By SoftwareEntry Point
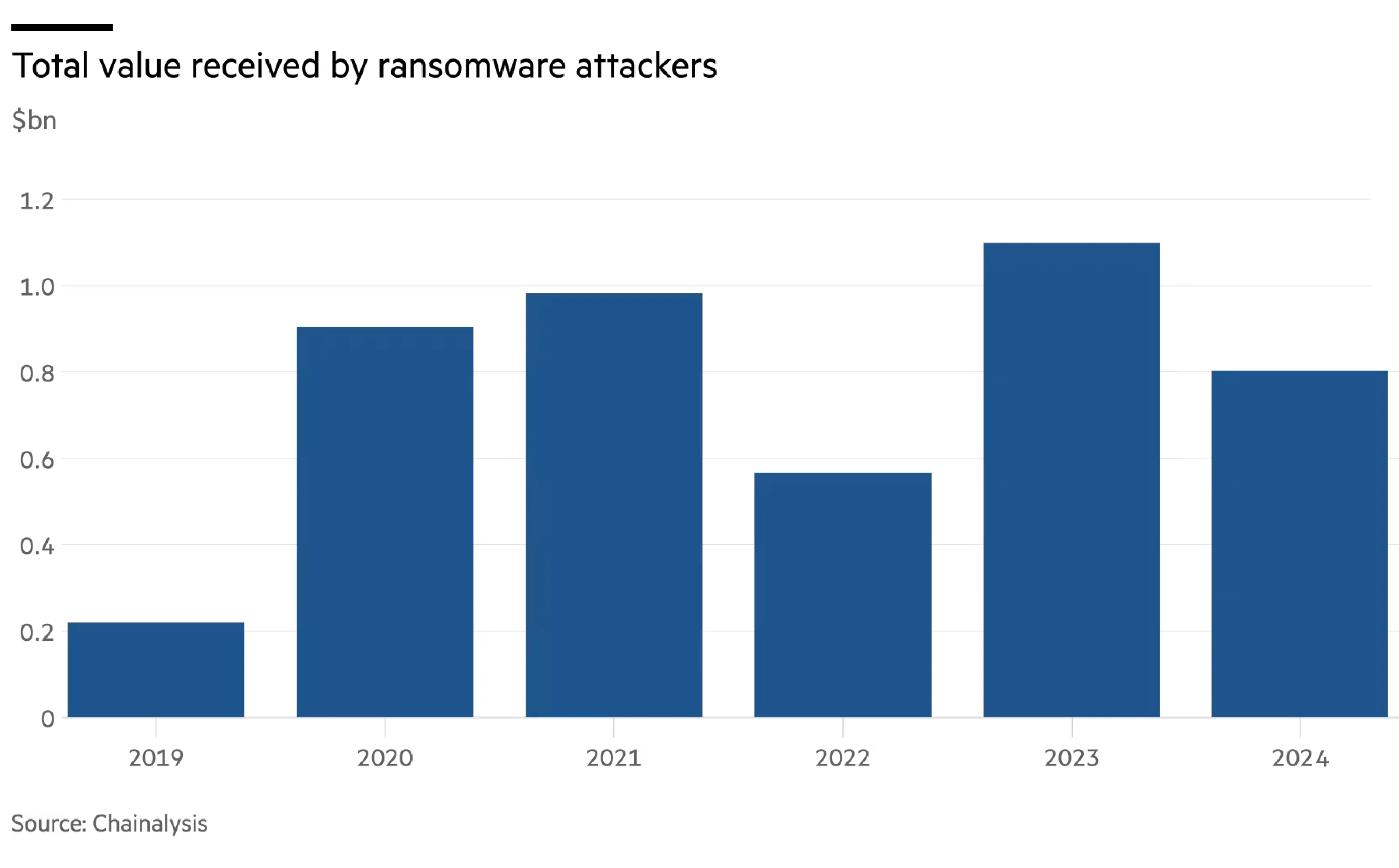
Cost of Breaches
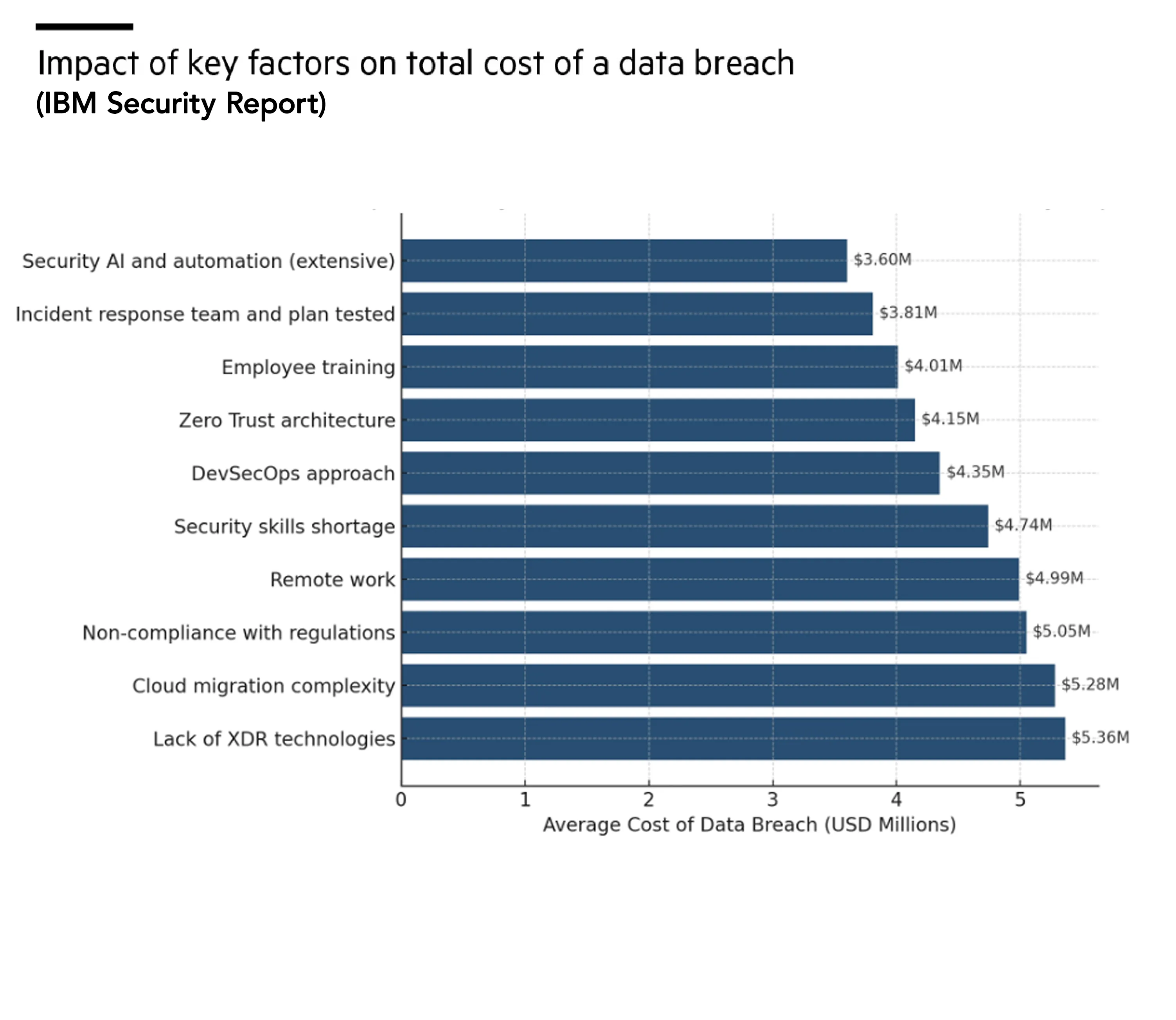
IBM's 2024 research found the average cost of a data breach to be $4.88 million. Companies paying ransoms saw minor savings and faced significant risks, with a report from Infosecurity stating that 78% experiencing repeat attacks. Paying ransoms often encourages further criminal activity and indicates inadequate security measures. This recurrence suggests companies might not sufficiently enhance their cybersecurity defenses post-attack, making them vulnerable targets. The findings emphasize the severe financial impact of breaches and the perilous cycle companies may enter by paying ransoms. Robust cybersecurity services and proactive threat management are crucial to mitigating the risks and costs associated with data breaches.

How Data Protection Services in Detroit Can Safeguard Your Company
Cloud-first and digital-first businesses may find this task easier than on-premises or legacy businesses, but they will still require a solution. So, choose Bizionic cybersecurity services Detroit as your partners.

Incident Response Plan.
Businesses require a data replication plan to safeguard their information when switching platforms. You can discuss this with our team of skilled experts who know how to isolate the breach, minimize the damage, and restore your systems.

Modernize your infrastructure.
Cloud-based solutions frequently provide superior data replication and security capabilities compared to on-premise systems.

WHY DO YOU WAIT?
Proceed to the next step. Let our professionals assist you
with finding the best solution.
FAQ'S
What are the benefits of using data security services in Detroit?
Bizionic's data security services in Detroit help businesses prevent data loss, ensure regulatory compliance, and protect customer trust by securing sensitive information from cyber threats.
How does danger detection and prevention help my business?
The danger detection and prevention provides real-time monitoring and immediate alert for suspicious activity, allowing them to respond immediately to potential cyber threats before proceeding.
How many times should I evaluate cyber risk in Detroit?
We recommend a cyber risk evaluation after an annual or necessary system upgrade, data breach, or regulatory changes in Detroit.
Why select business technologies for cyber security in Detroit?
Bizionic Technologies provides end-to-end cyber security services, including data security, threat detection, and cyber risk assessment in prevention and recovery, which are all planned and strategized to meet the unique needs of your business.
SERVICES
- Progressive Web App Development |
- Mobile App Development |
- Game Development |
- CRM Solutions |
- e-Commerce Development |
- Azure Services |
- Amazon Web Services |
- Data Science and Analytics Services |
- Enterprise Mobility Solutions |
- Cloud Consulting Services |
- Cyber Security |
- Cloud Infrastructure Setup and Management |
- Blockchain Development Services |
- AI Research and Development |
MARKETING
- Search Engine Optimization (SEO) |
- Pay Per Click (PPC) Services |
- Digital Marketing |
- UI/UX Services |
- Video Production |
- Content Marketing |
- Email Marketing |
- Influencer Marketing |
- Brand Marketing |
- E-Commerce Store |
- Payment Gateway |
- Voice Commerce |
- Chatbots Commerce |
- Customer Service Automation |
- Event Management |
- Campaign Monitoring |
- Layout Wireframes |
- Technical Analysis |
- Media Planning And Buying
TECHNOLOGIES
- Symfony |
- Drupal |
- MS Dynamics CRM |
- Salesforce |
- Sugar CRM |
- Shopify |
- SharePoint |
- Android Games |
- iOS Games |
- Website Development |
- Database Management |
- WordPress |
- Craft |
- Magento |
- Magento 2 |
- Quality Analyst |
- Unity 3D |
- Joomla |
- Opencart |
- WooCommerce |
- BigCommerce |
- NopCommerce |
- VirtueMart |
- Zencart
INDUSTRIES
- Startups Ecosystem |
- Real Estate |
- B2B Solutions |
- B2C Solutions |
- Healthcare |
- Travel & Hospitality |
- Banking & Finance |
- Media & Publishing |
- Education & e-Learning |
- Food & FMCG |
- Automotive |
- Retail and E-Commerce |
- Manufacturing |
- Telecommunications |
- Energy and Utilities |
- Government |
- Nonprofits |
- Professional Services |
- SaaS (Software as a Service) |
- Consumer Electronics |
- Fashion and Apparel |
- Agriculture







